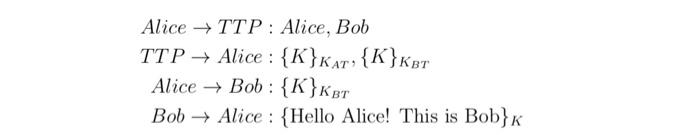Shed on Twitter: "The 40-page Shed feature in BOB Magazine is now on our website. https://t.co/Gn9FbXuyqp https://t.co/JLHO7a6NKv" / Twitter

Amazon.com : SWACC Rainbow Colors Straight Short Hair Bob Wig Synthetic Colorful Cosplay Daily Party Flapper Wig for Women with Wig Cap : Beauty & Personal Care
2021 Women's Conference USSSA Update after the Conference Championship! - www.softballcenter.comwww.softballcenter.com

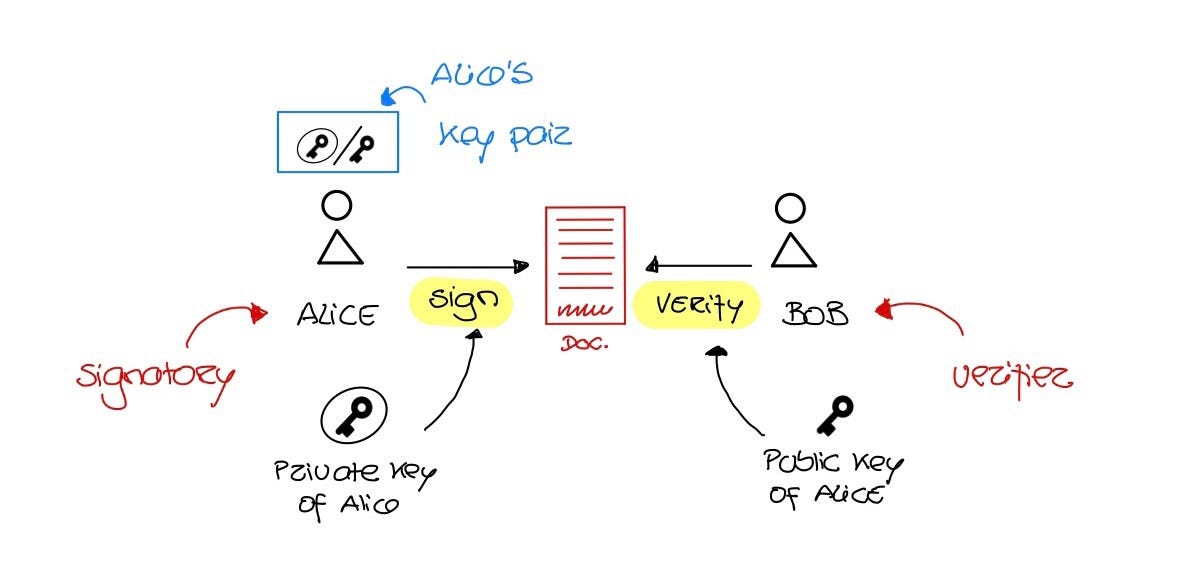
Threats to Modern Cryptography and State-of- the-Art Solutions Kenny Paterson Information Security Group. - ppt download
![PDF] A Hierarchical Trusted Thir d-Party System for Secure Peer-to-Peer Transactions | Semantic Scholar PDF] A Hierarchical Trusted Thir d-Party System for Secure Peer-to-Peer Transactions | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/f5e9dd671605683559b5d880d9ac04a78d3fd02b/23-Figure7-1.png)
PDF] A Hierarchical Trusted Thir d-Party System for Secure Peer-to-Peer Transactions | Semantic Scholar
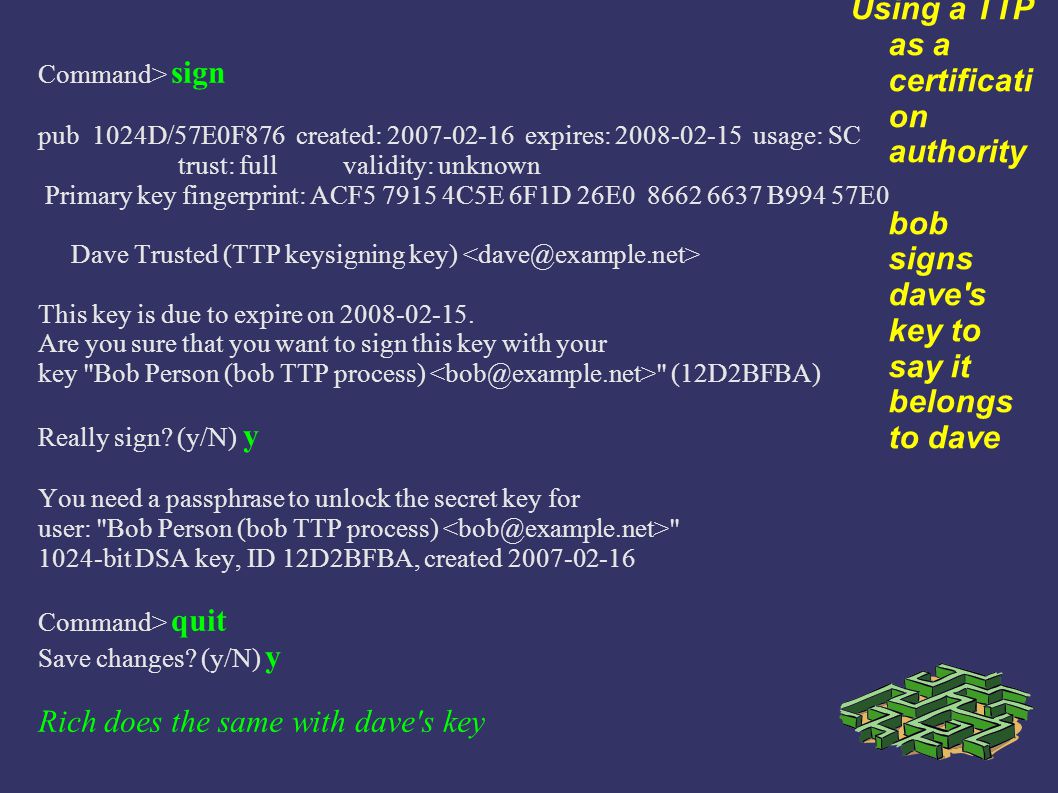
Using GPG - the GNU Privacy Guard Why does a security professional need this skill ? 3 GPG HOWTO's Use by checking Correspondents' Keys Directly Using. - ppt download
![PDF] A Hierarchical Trusted Thir d-Party System for Secure Peer-to-Peer Transactions | Semantic Scholar PDF] A Hierarchical Trusted Thir d-Party System for Secure Peer-to-Peer Transactions | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/f5e9dd671605683559b5d880d9ac04a78d3fd02b/16-Table1-1.png)